The cybersecurity industry is booming. As news headlines fill with stories of data breaches, ransomware attacks, and state-sponsored hacking, the demand for skilled professionals to defend our digital infrastructure has never been higher.
If you are looking to enter this field, you might be overwhelmed by the various job titles: Penetration Tester, Security Architect, CISO, Forensics Investigator. But if you ask, “What is the most common, most popular entry point, and the heartbeat of most security teams?” the answer is almost always the same.
The Cybersecurity Analyst.
Often called the “first line of defense” or the “digital detectives” of the IT world, Cybersecurity Analysts are essential to any modern organization. But what do they actually do, and is it the right career path for you?
Here is a deep dive into the role of a Cybersecurity Analyst.
The Job Description: The Sentinel
At its core, a Cybersecurity Analyst is responsible for protecting an organization’s computer networks and systems e.g. cloud. If you imagine an organization’s network as a castle, the Analysts are the guards on the wall, constantly scanning the horizon for approaching threats and checking the gates for weaknesses.
They don’t just wait for an attack to happen; they proactively monitor networks for suspicious activity, analyze security alerts, and respond to incidents before they become catastrophes.
Their goal is to ensure the confidentiality, integrity, and availability of data.
Key Responsibilities
While the specifics vary depending on the size of the company, a Cybersecurity Analyst’s core responsibilities usually include:
-
Threat Monitoring: Using sophisticated software (like SIEM tools) to monitor network traffic for anomalies 24/7.
-
Incident Triage: When an alert goes off, they are the first to investigate. Is it a false positive, or is it a real threat?
-
Vulnerability Scanning: Regularly testing systems to find weak spots (like unpatched software) before hackers do.
-
Threat Intelligence: Staying up-to-date on the latest hacker tactics, techniques, and procedures (TTPs) globally.
-
Reporting and Documentation: Translating technical data into clear reports for management and documenting incidents for future reference.
-
Security Policy maintenance: assisting in configuring firewalls, antivirus software, and data encryption tools.
What a “Day in the Life” Looks Like
No two days are exactly alike in cyber, but a typical day for an analyst in a Security Operations Center (SOC) often follows a rhythm:
The Morning: You log in and immediately check the “dashboards.” You review alerts that came in overnight. You might spend the first two hours sifting through logs that look suspicious, quickly determining that 95% of them are normal network noise (false positives).
Mid-Day: You attend a stand-up meeting with the IT team to discuss ongoing projects or a new software deployment that needs a security review. You then spend time running a scheduled vulnerability scan on a specific segment of the network.
The Afternoon: You receive a notification from an employee reporting a suspicious email. You analyze the email header, safely detonate the attachment in a “sandbox” environment, determine it is a phishing attempt, and block the sender across the company network.
End of Shift: You finalize your shift log, documenting the phishing incident, and hand over pending items to the next shift analyst.
The Intensive Situation: When the Alarm Bells Ring
The routine described above is the “peace time” scenario. But the real test of an analyst is during a “wartime” event—a live security incident.
Imagine it’s 2:00 PM on a Tuesday. Suddenly, your SIEM dashboard lights up red. Multiple user accounts are being locked out simultaneously, and servers are showing massive spikes in encrypted file activity. This looks like Ransomware.
The shift is instantaneous. The atmosphere goes from quiet concentration to controlled chaos.
-
Adrenaline kicks in: You move immediately into incident response mode.
-
Containment: You work furiously with network engineers to isolate infected environments or machines, severing them from the main location to stop the spread.
-
Forensics on the fly: You are trying to identify “Patient Zero”- where did the infection start? Was it an email? A USB drive? or an exe file.
-
Communication: You are on emergency conference calls with IT leadership, translating technical crises into business impacts.
During these intensive situations, analysts might work 12-16 hour shifts until the threat is neutralized. It is high pressure, requires calm under fire, and relies heavily on teamwork.
Key Technical Skills Required
You cannot protect a network if you don’t understand how it works. To be a successful Cybersecurity Analyst, you need a solid technical foundation:
-
Networking Fundamentals: A deep understanding of TCP/IP, routing, switching, DNS, and VPNs is non-negotiable. You need to know how data moves.
-
Operating Systems: Proficiency in both Windows and Linux environments. You need to know what “normal” looks like in these OSs to spot what is “abnormal.”
-
SIEM Proficiency: Experience with Security Information and Event Management tools (like Splunk, Azure Sentinel, or Elastic) is crucial. This is where you will live.
-
Incident Response Frameworks: Understanding the lifecycle of an incident (Preparation, Detection, Containment, Eradication, Recovery).
-
Basic Scripting: Knowing Python or PowerShell is increasingly necessary to automate repetitive tasks and parse logs faster.
Security Operations Center (SOC) – The most popular term
Think of a Security Operations Center (SOC) as the “Mission Control” or the “Digital War Room” of an organization.
While the Cybersecurity Analyst is the person doing the work, the SOC is the centralized hub where that work happens. It’s a command center staffed by a team of security professionals who monitor an organization’s entire IT infrastructure 24/7 to detect, analyze, and respond to cyber threats.
Here is a breakdown of how a SOC actually functions:
The Three Pillars of a SOC
A SOC isn’t just a room full of monitors; it’s a combination of three critical elements:
-
People: Security analysts (Levels 1, 2, and 3), incident responders, forensic investigators, and SOC managers.
-
Processes: The “playbooks” or step-by-step instructions on how to react when a specific threat (like a malware infection) is detected.
-
Technology: The heavy-duty tools, primarily the SIEM (Security Information and Event Management) system, which collects logs and data from every corner of the company’s network.
What does a SOC actually do?
If you walked into a SOC today, the team would be focused on these core functions:
-
Continuous Monitoring: Scanning the network around the clock. Hackers don’t take weekends off, so neither does the SOC.
-
Alert Ranking (Triage): Not every alert is a crisis. The SOC sifts through thousands of “pings” to find the one that actually matters.
-
Incident Response: When a real threat is confirmed, the SOC coordinates the “counter-attack” to shut down the breach.
-
Root Cause Analysis: After a threat is gone, the SOC investigates how it got in so they can patch the hole for good.
-
Compliance: Ensuring the company is following legal rules about data protection (like keeping records of who accessed what).
The “SOC Levels” (Hierarchy)
Most SOCs operate on a tiered system to manage the workload:
| Tier | Role | Responsibility |
| Tier 1 | Triage Analyst | Monitors alerts, determines if they are real or “false positives.” |
| Tier 2 | Incident Responder | Deep-dives into real attacks and works to contain/neutralize them. |
| Tier 3 | Threat Hunter | Proactively searches the network for hidden hackers who haven’t set off alarms yet. |
| Manager | SOC Lead | Oversees the whole operation and communicates with company executives. |
Why is it important?
Without a SOC, an organization is “flying blind.” Most companies that get hacked don’t even realize they’ve been breached for months. A SOC reduces that “dwell time”—the time a hacker spends inside a network—from months down to minutes.
Fun Fact: Some modern SOCs are “Virtual SOCs” (vSOC), where the team is entirely remote, but the function remains exactly the same!
Would you like to know about the specific certifications you’d need to get hired into a SOC?
If you have zero experience, these build your “security vocabulary” and prove to recruiters that you understand the basics.
-
CompTIA Security+: Still the “Gold Standard” for entry-level roles. It is appearing in over 70% of entry-level job postings in Australia. It covers a broad range of topics from risk to basic networking.
-
Google Cybersecurity Professional Certificate: A very popular, low-cost entry point. It’s practical, uses Python and SQL, and gives you a 30% discount on the CompTIA Security+ exam.
-
Microsoft SC-900 (Security Fundamentals): Crucial for the NZ/AU market. Most corporate environments in this region run on Microsoft 365 and Azure. Knowing how Microsoft handles identity and compliance is a massive advantage.
Pro-Tip for the AU/NZ Market
In Australia and New Zealand, employers value Azure/Microsoft skills highly because of the local dominance of the Microsoft cloud ecosystem.
If I were starting today, I would pursue this path:
-
SC-900 (Quick win, cheap)
-
Security+ (The “must-have” for HR)
-
BTL1 (The “proof” you can do the job)
Final Thoughts
The Cybersecurity Analyst role is popular for a reason. It offers a dynamic work environment, excellent earning potential, and the genuine satisfaction of knowing your work protects people and businesses. It is a challenging front-line role, but for those with curiosity and a technical mindset, it is one of the most rewarding careers in tech.
What is Industry Connect?
Industry Connect is an IT/Software Career Launchpad that has everything you need
to kick-start your IT/software career in AU, NZ, UK, IE, SG, HK, IN, ID, VN & PH.

We have been helping career changers, recent IT graduates and people with a career gap
to start their IT/software careers.
Over the years, we have helped hundreds kick-start an IT/software career.
(Verifiable evidences are available on this website)
OUR CORE
We are an innovative software training school backed by global/local software companies.
Our ecosystem is an incubation process that supports our participants until they launch
a tech career.
OUR PROGRAMMES
Our Job-Ready training programmes focus on:
- Software Development
- Business Intelligence (or Data Analyst)
- Test Analyst
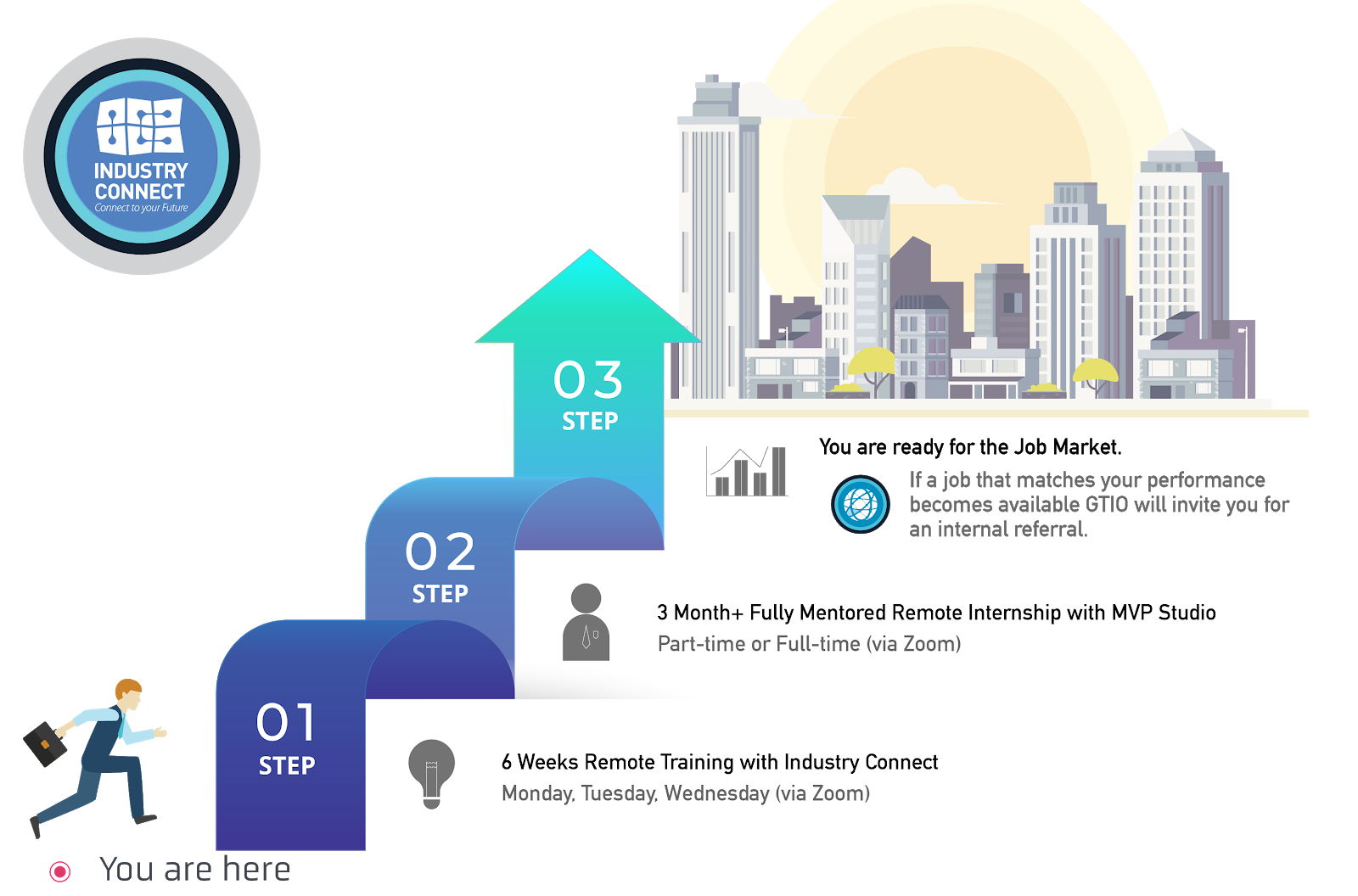
PROGRAMME STRUCTURE
- Six Weeks Training Classes (Practical Tech Skills)
- Three Months (or more) Structured Internship on Large Commercial-Scale Projects (flexible hours)
- Employer Network (job analysis and internal referral if goals are met)
You can join us via Zoom (live face-to-face meeting) remotely from anywhere and
“download” the valuable knowledge & experiences from our tech experts across
different tech centres.
Watch 300+ Stories of Career Starters in IT/Software
- Career Changers & Switch to IT
- Recent Graduates
- People with a Career Gap
- New Software Developers
- New BI or Data Analysts
- New Test Analysts
Click the image to watch those who changed their careers to IT, had gap years and recent IT graduates.